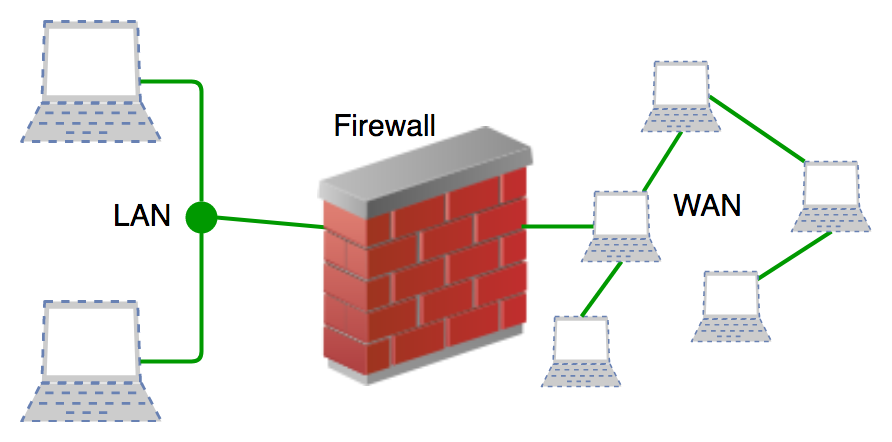
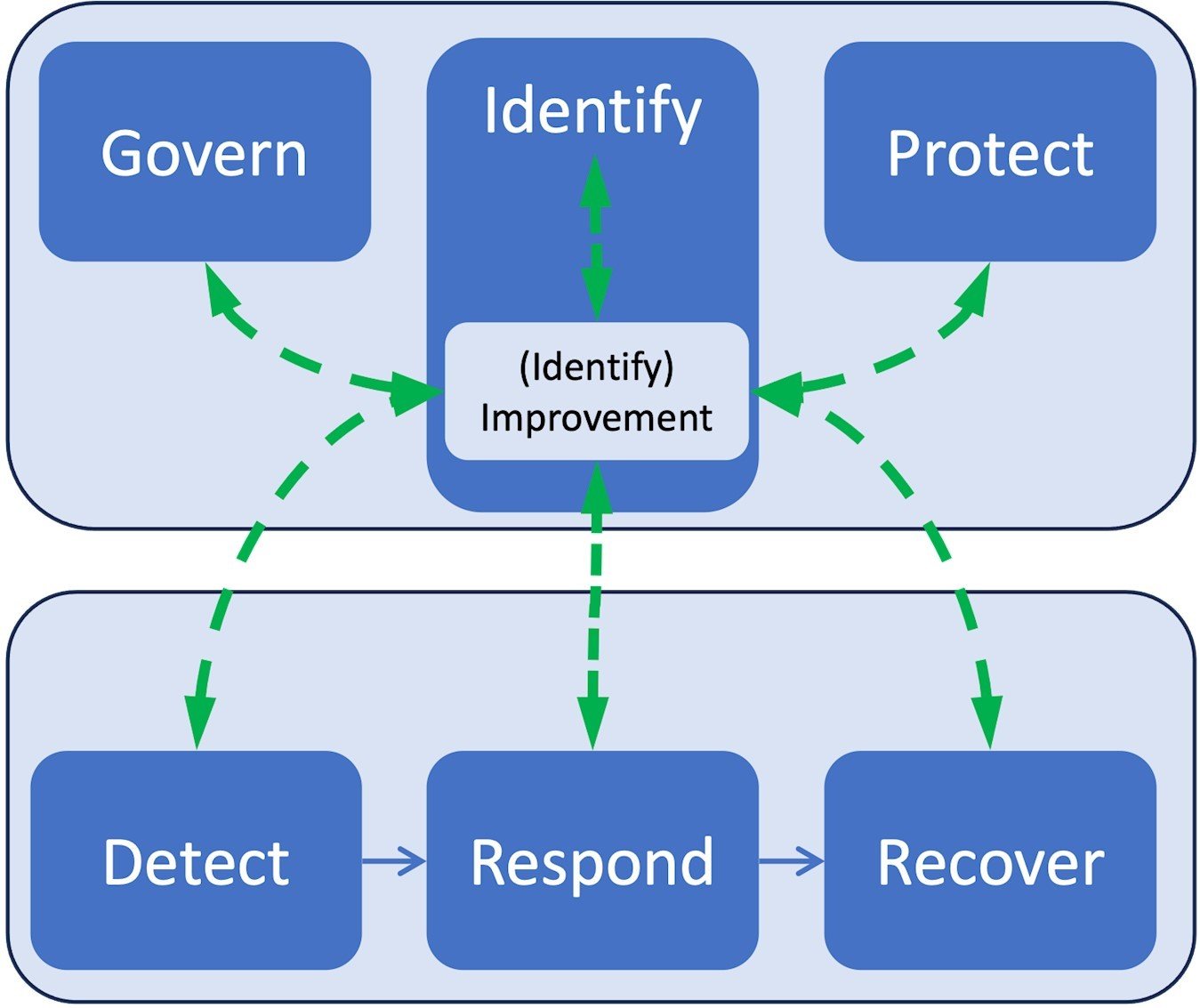
Our Cybersecurity Tech Stack
We leverage industry-leading tools and platforms to deliver secure, scalable, and future-ready cybersecurity solutions for enterprises worldwide.
🛡️ Threat Detection Tools
 Suricata
Suricata
 Snort
Snort
 Wireshark
Wireshark
🔐 Security Management Platforms
 Splunk
Splunk
 IBM QRadar
IBM QRadar
 Elastic Security
Elastic Security
🌐 Network Security
 OpenVPN
OpenVPN
 pfSense
pfSense
 Nmap
Nmap
🖥️ Endpoint Protection
 Symantec
Symantec
 McAfee
McAfee
 Bitdefender
Bitdefender